Google raises top bounty for its websites by 50 percent to $31k
- 03 March, 2017 08:04

Google is offering up more cash for security researchers and has revealed which countries are receiving the most rewards from its programs.
Google will now pay $31,337 to researchers who find a remote code execution bug affecting its websites, including Google, YouTube and Blogger domains.
That’s just over a 50 percent rise on the former top payout of $20,000 for its vulnerability rewards program. The top pay goes to remote execution and other equally severe issues that would allow attackers to breach its servers. Google has also increased its payout for “unrestricted file system or database access” from $10,000 to $13,337, representing just over a 30 percent rise.
“Because high severity vulnerabilities have become harder to identify over the years, researchers have needed more time to find them,” Josh Armour, a security program manager at Google, said of the higher rewards.
Google announced the higher payouts to mark its sponsorship of the Nullcon security conference in Goa, India, which starts on Friday.
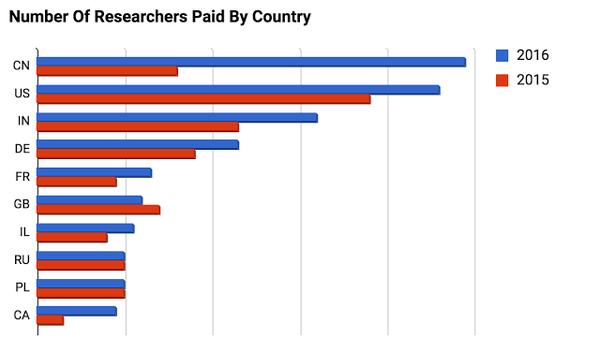
The search company has revealed new details about who’s earning the most from its bug bounties, which have covered websites and Chrome since 2010, and since mid-2015, Android. Last year it paid $3 million to researchers, up from $2 million in 2015.
A chunk of that increase may have gone to researchers in China who, judged by the number of researchers paid by country, jumped from fourth position in 2015 to first in 2016. In 2015, prior to a full year of the Android bug bounty running, the US was leading, followed by India, and Germany.
“We have noticed a 3X increase in reports from Asia, making up 70% of the Android Security Rewards for 2016,” wrote Armour.
Others in the top 10 in 2016 in descending order were the US, India, Germany, France, Great Britain, Israel, Russia, Poland, and Canada.
Given Google’s focus on India this week, Armour also highlights that it tripled its total rewards to researchers in India, and doubled the average payout both per researcher and per reward.
Software firms, and increasingly traditional organizations such as the US Department of Defense, have found bug bounty programs a useful tool for improving the security of certain tech infrastructure.
But while commercial and government organizations can stump up the cash for bug bounty programs, the security of some open source software projects that are critical to the internet have been neglected due to a lack of resources.
The security of open source software came under the spotlight after the discovery of the OpenSSL bug Heartbleed, which prompted major tech firms, including Microsoft and Google, to fund the Linux Core Infrastructure Program.
Open source projects could get more help now thanks to a new free program by bug bounty operator HackerOne, which runs bounties for DoD, Tesla, and many others.
Dubbed the HackerOne Community Edition, the program offers eligible open source projects vulnerability submission, coordination, duplicate bug detection, analytics, and bounty programs.
Open source projects that already use its platform include Ruby, Rails, Discourse, Django, GitLab, Brave, and Sentry.

