Newsweek Twitter hack is a sign of the times
- 11 February, 2015 08:50
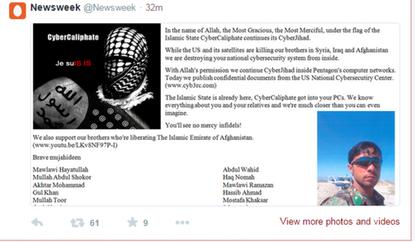
Newsweek's page as it appeared on Twitter after it was hacked.
The Twitter accounts of two more companies -- Newsweek and the International Business Times -- were compromised on Tuesday, showing Twitter's attractiveness to hackers despite its cybersecurity features.
The @Newsweek account was hacked at 10:45 a.m. Eastern time by a group identifying itself as the "Cyber Caliphate," claiming affiliation with the militant group known as ISIS or the Islamic State.
The account, which has more than 2.5 million followers, was compromised for nearly 15 minutes, during which time messages were tweeted threatening First Lady Michelle Obama and praising "cyber jihad," according to an account of the incident published by Newsweek. The account's profile picture and banner were changed to images of a masked man and the Black Standard flag typically flown by ISIS.
Also, ibtimes.com, the website of the International Business Times, was apparently hacked by the same group, Newsweek said. Newsweek and the International Business Times share a parent company, IBT Media.
The rate at which established companies, media outlets and public figures get hacked on Twitter is becoming exasperatingly high. The Twitter account of the U.S. Central Command, a top military security unit, was hacked last month, also by ISIS sympathizers. The Twitter and Instagram accounts of singer Taylor Swift have also been compromised.
Later on Tuesday, the Twitter account of the company's own chief financial officer, Anthony Noto, might have been hacked, as it sent out spammy tweets. A Twitter spokesman declined to say whether the account had actually been hacked, though he pointed to this explainer on compromised accounts.
Any social media account is at risk of getting compromised, but attackers see immense value in taking over a Twitter account because of the site's public-facing nature. These types of incidents, especially on Twitter, are likely to continue unless businesses and individuals adopt smarter measures for how they secure their accounts.
Hackers use a variety of methods to break into accounts, but two strategies in particular stand out: brute force and phishing. For brute force, there are password-cracking tools online that allow attackers to sort through a dictionary and guess the password. The attacker can set up the system in the cloud and program it to make password guesses gradually, for example over a period of weeks or months, and from different IP addresses, so that the site in question does not lock them out, said Ian Amit, vice president of ZeroFOX, a cybersecurity company that monitors suspicious activity on social media.
Phishing attacks trick account holders into entering login credentials through an email that appears to be coming from a particular site, but is not.
Security experts often advise people to choose lengthy passwords and use two-factor authentication when it is offered by a site. Two-factor authentication technology prompts users to enter a special code, usually sent to their personal mobile devices, when they log in. Many online services like Google and Facebook offer it, with Twitter rolling it out in 2013.
Two-factor authentication is easy enough when you're the only person using an account, because the code is sent to your own phone. But it's trickier to employ for a business account to which multiple employees, using different phones, have access.
In this case, businesses should consider using a centralized dashboard application, like Hootsuite or GroupTweet, to manage their Twitter account, said Amit of ZeroFOX. Pick a complicated password to log in to Twitter via the centralized app. From there, a business can give permission for individual employees to access the company account using two-factor logins.
Also, companies should take a wider look at their online presence across social media, Amit said. If the CEO (or CFO) has a weak password and does not use two-factor authentication for a personal account, that might present an easy target for hackers, who could then spread misinformation or access other accounts to which the executives have access.
Zach Miners covers social networking, search and general technology news for IDG News Service. Follow Zach on Twitter at @zachminers. Zach's e-mail address is zach_miners@idg.com

