 Credit: Gerd Altmann
Credit: Gerd Altmann
Microsoft recently announced that 99.9% of the attacks on Office 365 credentials can be stopped by enabling multi-factor authentication (MFA). They should have made it clear that you need to take one more action and disable basic or legacy authentication.
Basic or legacy authentication is what most people use when they log into websites and networks: a username and a password. If someone cracks that, has harvested the hash value and can reuse it, or used brute force and password spraying techniques to gain access, they are in. They often don’t even have to “crack” the password; they already have it. Most people reuse passwords, so once an attacker has breached a database, they can try that password on your server or other sites.
So, you need to turn off legacy authentication when implementing MFA. What are the consequences to that? Third-party tools that plug into your online applications might no longer work. This is honestly a good thing, because you need to demand that vendors stop using an old insecure method to connect to your information. If they use legacy authentication, they are basically using IMAP, POP, SMTP and other older protocols to connect.
Ensure that you are using newer Outlook clients to connect to Office 365. Outlook 2010 is no longer supported to connect to Office 365 even though some still use the platform. If you disable legacy authentication on Outlook 10, it won’t be able to connect. The user impact plays out in various scenarios.
Disable basic authentication in Office 365 and Exchange
I described how to disable basic authentication on Office 365 earlier, but what about on-premises Microsoft Exchange? Doesn’t it have the same risks as cloud implementations of Exchange? In a word, yes. Attackers can use some of the same tools they use to evaluate risks on Office 365 on your on-premises Exchange Server. That’s why you should disable legacy authentication for it as well. You’ll need Exchange 2019 to do so. Prior versions of Exchange are not able to perform the settings.
Let’s review what you need to do to disable the potential security hole. First, determine what version of Outlook or mail platforms you use to connect to Exchange. The following platforms can connect to Exchange without basic authentication. This is true for both Office 365 as well as Exchange 2019. You’ll need these updated clients to enable modern authentication.
- Outlook 2013 or later
- Outlook 2016 for Mac or later
- Outlook for iOS and Android
- Mail for iOS 11.3.1 or later
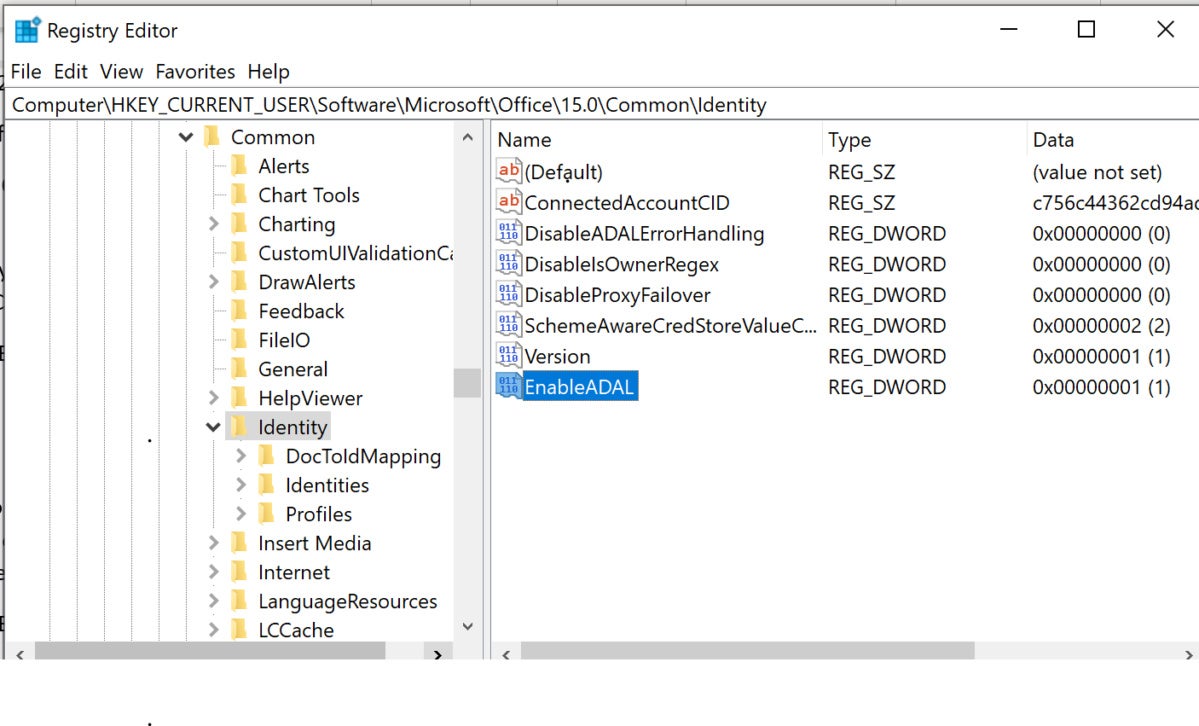
For Outlook 2013 you need to enable its ability to support modern authentication through a registry key. From the Registry Editor, go to “HK Current user,” then to “Software,” then to “Microsoft,” then to “Office,” then to “15.0,” then to “Common,” then to “Identity.” Add the value “EnableADAL” with the “Reg_Dword” value of “1.”
HKCU\SOFTWARE\Microsoft\Office\15.0\Common\Identity\EnableADAL
REG_DWORD
1
Next, set the following value. Go to “HK Current” user, then to “Software,” then to “Microsoft,” then to “Office,” then to “15.0,” then to “Common,” then to “Identity.” Add the value “Version” with the “Reg_Dword” value of “1.”
HKCU\SOFTWARE\Microsoft\Office\15.0\Common\Identity\Version
REG_DWORD
1
Push out the settings via Group Policy or registry keys.
 Susan Bradley
Susan Bradley
Disable basic authentication using the Registry Editor
Now that you have Outlook 2013 set to support modern authentication, you can also roll out the setting in either Office 365 or Exchange 2019. The mailboxes must be hosted on mailboxes that are on an Exchange 2019 CU2 server. To block legacy authentication, prepare authentication policies. In the Exchange management shell, enter the following PowerShell command:
New-AuthenticationPolicy -Name "Block Legacy Auth" -BlockLegacyAuthActiveSync -BlockLegacyAuthAutodiscover -BlockLegacyAuthImap -BlockLegacyAuthMapi -BlockLegacyAuthOfflineAddressBook -BlockLegacyAuthPop -BlockLegacyAuthRpc -BlockLegacyAuthWebServices
The command blocks the following protocols:
- BlockLegacyAuthActiveSync blocks the use of Exchange Active Sync (EAS), which some email clients use on mobile devices.
- BlockLegacyAuthAutodiscover blocks the use of Autodiscover to find and connect to mailboxes in Exchange. This also blocks attackers from being able to enumerate and discover mailboxes to more easily attack Exchange servers.
- BlockLegacyAuthImap blocks the use of IMAP email clients. Attackers often use IMAP in password spray attacks.
- BlockLegacyAuthMapi is used by Outlook 2013 and later for MAPI over HTTP.
- BlockLegacyAuthOfflineAddressBook blocks the ability to download address list collections that Outlook uses over basic authentication.
- BlockLegacyAuthPop is used by POP email clients.
- BlockLegacyAuthRpc is used by Outlook 2016 and earlier for Outlook anywhere (RPC over HTTP).
- BlockLegacyAuthWebServices blocks the use of a programming interface that’s used by Outlook, Outlook for Mac, and third-party apps as part of Exchange Web Services (EWS)
Once you’ve set up the policy, then you need to assign the policy to users. You can assign the policy individually or via attributes. If your usernames do not have spaces, you can build a text file that injects the usernames into the script.
$BLA = Get-Content "C:\Scripts\ListofUsersBlockLegacyAuth.txt"
$BLA | foreach {Set-User -Identity $_ -AuthenticationPolicy "Block Legacy Auth"}
Prepare a text file of all the users in your organization for whom you wish to block legacy authentication, save the list to ListofUsersBlockLegacyAuth.txt, and run the script.
If you want to set this as the default policy, use the following command that all new users to the organization will only accept modern authentication.
Set-OrganizationConfig -DefaultAuthenticationPolicy "Block Legacy Auth"
This sets the entire organization to block legacy authentication going forward.
Bottom line, plan on a future where IMAP, POP and older protocols are banned from your network. Even if you can’t disable legacy authentication now, evaluate the potential in the future. Review all the third-party tools that you use to connect to Exchange or add to Exchange and review if they can work without IMAP or POP connectivity.
As always, don’t forget to sign up for TechTalk from IDG the new YouTube channel for tech news of the day.