Three years ago the Obama administration mandated secure HTTPS connections for all .gov websites by the end of 2016. Today, as the government shutdown under the Trump administration enters its 20th day, dozens of HTTPS .gov sites are using expired digital Transport Layer Security (TLS) certificates.
NASA, The US Department of Justice, and the Court of Appeals are among the government organizations with sites that are using expired digital certificates that would normally have been renewed were it not for the shutdown, which affects some 380,000 public employees.
According to UK internet firm, Netcraft, 80 TLS certificates for HTTPS for .gov sites have now expired since the shutdown. Visitors to these sites will see a full page or “interstitial” warning in the browser that a connection is not secure and a recommendation not to proceed.
One example is the Justice Department HTTPS site ows2.usdoj.gov, whose certificate expired 23 days ago, just before the shutdown commenced.
As noted by Netcraft’s Paul Mutton, current expired certificates and future ones as the shutdown drags on, could create a situation that’s ripe for phishing attackers to exploit.
A key problem arises from variations in the way .gov sites have implemented the HTTPS Strict Transport Security (HSTS) policy. HSTS ensures that browsers never use an HTTP connection where HTTPS is available, protecting the user from potential man-in-the-middle attacks.
Chrome and Firefox will display the same interstitial, advising that a connection is not private whether or not HSTS correctly. Both also feature an “Advanced” button.
However, on sites where HSTS is implemented incorrectly, clicking Advanced allows user to click through to the site with an expired certificate, while the site that implements HSTS correctly will only display information about risks but not allow the user to proceed.
The Justice Department’s usdjo.gov domain and all its subdomains are examples of correctly implemented HSTS, because they’re all included in Chromium’s HTTPS Strict Transport Security (HSTS) preload list.
Users simply can’t proceed to the DJO site because of the expired certificate, which may be frustrating for the user, but Mutton argues in this case security may trump convenience.
“If users were to ignore such warnings, they would be vulnerable to the type of man-in-the-middle attacks that TLS certificates were intended to combat,” writes Mutton.
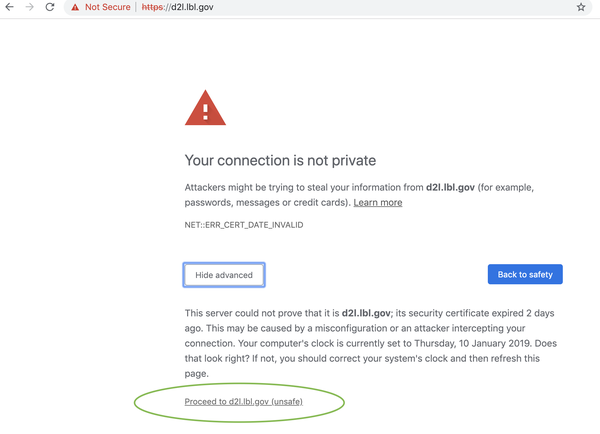
But sites like the Berkeley Lab website at https://d2l.lbl.gov and NASA’s https://rockettest.nasa.gov/ are not included in the HSTS preload list. Chrome users here have the option to proceed to the site despite their respective certificates having expired and not renewed during the shutdown.
And while the NASA site leads to an information page that poses little risk, the Berkeley Labs site is particularly opens a login page. If the use clicks the “Not Secure” icon next to the address bar there is a warning not to enter passwords, but a person who needs to use the site can do so and could end up “foolishly” doing so anyway.
Mutton notes that encouraging users to ignore browser warnings could make them more susceptible to man-in-the-middle attacks.
“As more and more certificates used by government websites inevitably expire over the following days, weeks — or maybe even months — there could be some realistic opportunities to undermine the security of all U.S. citizens,” writes Mutton.