
If only ransomware victims could choose their attackers as customers do, they might gravitate towards the ones with the best customer service.
Unfortunately, victims don’t get to choose which ransomware encrypts their files, but they still have one choice left: whether to pay for their files to be decrypted or accept their loss. This choice is why, Finnish security firm F-Secure argues in a new report, many ransomware gangs offer customer service levels akin to legitimate businesses, ranging from technical support to “discounts” to encourage payment.
“They’re disreputable, yet reputation is everything: without establishing a reputation for providing reliable decryption, their victims won’t trust them enough to pay them,” the firm notes of ransomware variants in the report.
As the firm highlights, most people would never wish to experience any form of customer service from a ransomware gang, and its standard advice remains for users not to pay the ransom but rather protect themselves by taking regular backups, running up-to-date software and using security software.
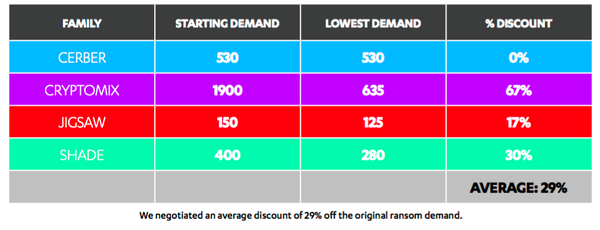
However, two interesting findings were that ransomware gangs regularly offer deadline extensions, and many are flexible on price. F-Secure was for example able to negotiate an on average overall 29 percent discount from three of the five ransomware samples in its review.
The five families of ransomware in the review included the text-to-speech using variant, Cerber, Cryptomix, Jigsaw, Shade, and Torrent Locker, which at one point had a sweet spot for Australian targets.
To assess each operation, F-Secure set up a bogus identity, called “Christine Walters”, a 40-something mother of two. “Christine” is not into tech and knows almost nothing about ransomware or Bitcoin, the currency that all ransomware asks for payment in. Under the guise of Christine, F-Secure’s team of ransomware reviewers then contacted each of the operators to see which family offered the best or least worst “customer journey from start to finish”.
And like a standard product review, F-Secure then scored each variant based on how easy or difficult the the operator was to contact, how responsive and helpful they were, and whether they were flexible on price and deadline. It also assessed each ransomware group’s user interface, looking at whether it was attractive and helpful, and whether it offered a free sample decryption.
Cerber scored the highest marks for its web pages, which F-Secure found were “detailed and informative” and offered user interface support for 12 languages. But while Cerber’s support was quick to respond to its queries, the operator wouldn’t budge on the price of $550 for the decryption key. Nor would Cerber help “Christine” with questions about how to make a payment in Bitcoin. t was however willing to extend the deadline.
F-Secure had more luck negotiating a deal with the operators of Cryptomix, which initially demanded payment of three Bitcoin (around $2,000) within 72 hours. F-Secure’s “Christine” protested the price and argued that most ransomware charged between $300 to $500. Cryptomix eventually knocked off $1,350 from the original asking price and also extended the payment deadline when asked.
One surprisingly helpful ransomware variant was Jigsaw, according to F-Secure. Besides immediately dropping the asking price from $150 to $125, Jigsaw helped F-Secure find the most suitable Bitcoin vendor for “Christine’s” supposed location and even offered to stay online and guide her through the payment process.
“It felt like I was dealing with a customer service agent from a legitimate business,” F-Secure’s reviewer said. “It seemed like he wanted to solve the case in a way that would work out best for me. Of course, ‘best’ would be never to have had files ransomed in the first place. But that aside.”
F-Secure notes in a disclaimer that it didn’t actually go through to make the payment and only used dumb files in its review, so Christine wasn’t as stressed out as many actual victims would be. Also, the company only assessed one variant of each family, which might not reflect the behaviour of other non-tested variants.